Securing Your Mobile App: Best Practices for Privacy and Data Protection
In our increasingly interconnected digital landscape, where smartphones have become an integral part of our lives, ensuring the security and privacy of user data has become paramount. As the number of mobile applications continues to soar, so does the need for developers to adopt robust security practices to protect sensitive information from falling into the wrong hands.

For many firms, mobile applications have been one of the most important sources of revenue. Their estimated revenue for 2023 is $935 billion, up from close to $693 billion in 2021. This extraordinary increase is, however, accompanied by dangers from cyberattacks. Security for mobile apps is essential because of this.
According to the Mobile Security Report 2021, 46% of employees downloaded at least one harmful application, and 97% of the organizations had experienced mobile-related assaults. It has given rise to several worries about the security of user data and the businesses that connect with brands for various reasons. During these interactions, they trade data with the brands on the applications, which can result in malicious exposure without adequate security measures.
What Are The Possible Threats To A Mobile Application?
It’s crucial to be aware of any potential hazards when creating mobile applications. These dangers emphasize the need for strong security measures to be put in place, including secure coding procedures, reliable authentication systems, encryption, secure network communications, regular security testing, and adherence to privacy laws. You may improve the security and integrity of your mobile application by being proactive in spotting and reducing these threats.
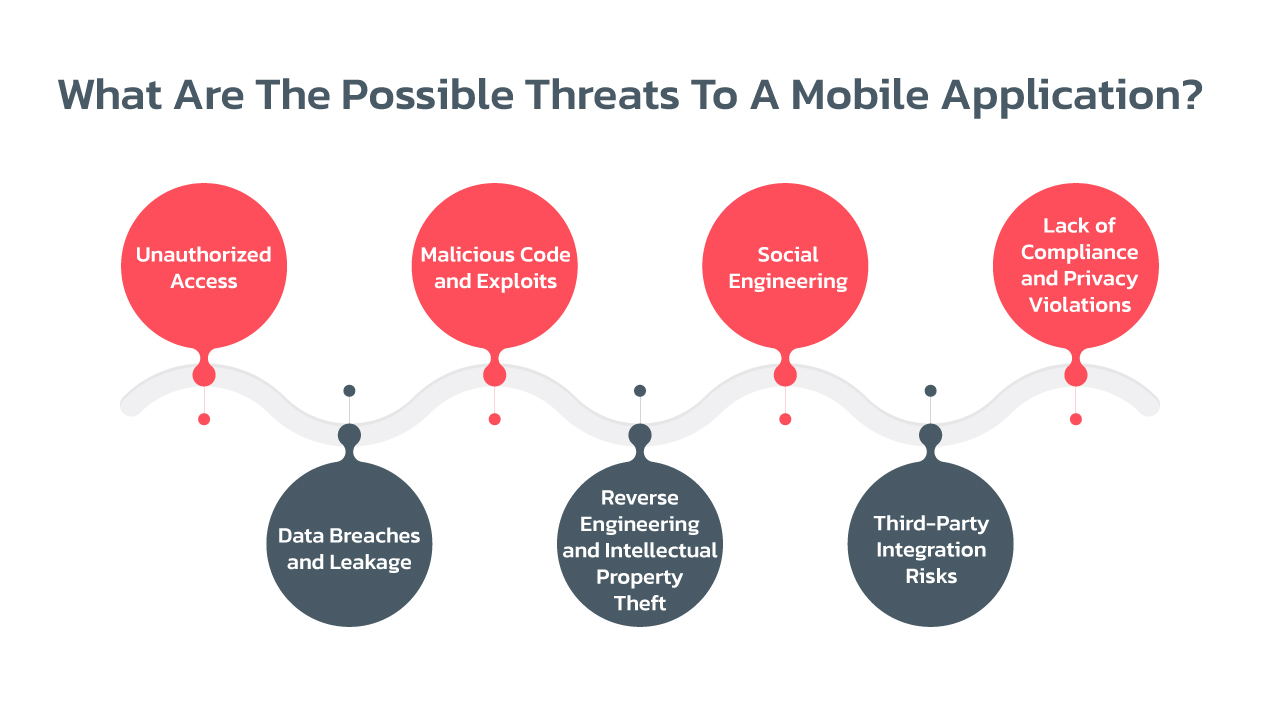
- Unauthorized Access:
- Brute force attacks: Automated attempts to guess usernames and passwords to gain unauthorized access to user accounts.
- Session hijacking: Exploiting vulnerabilities to gain control over a user’s active session and impersonating them.
- Jailbreaking/Rooting: Altering device settings to bypass security measures and gain unauthorized access to the application’s data.
- Data Breaches and Leakage:
- Insecure data storage: Storing sensitive user information in an unprotected manner, making it vulnerable to unauthorized access.
- Insecure data transmission: Transmitting data without encryption, allowing eavesdropping or interception by malicious entities.
- Improper access controls: Allowing unauthorized users or roles to access sensitive data or perform unauthorized actions.
- Malicious Code and Exploits:
- Malware: Malicious software designed to compromise devices, steal data, or perform unauthorized actions.
- Code vulnerabilities: Exploiting weaknesses in the application’s code, such as buffer overflows, SQL injections, or Cross-Site Scripting (XSS) attacks.
- Man-in-the-Middle (MitM) attacks: Intercepting communication between the app and servers to manipulate or steal data.
- Reverse Engineering and Intellectual Property Theft:
- Decompilation: Analyzing and reverse engineering the app’s code to extract sensitive information or exploit vulnerabilities.
- Intellectual property theft: Unauthorized copying, reproduction, or distribution of proprietary code, algorithms, or app features.
- Social Engineering:
- Phishing: Impersonating legitimate entities to deceive users into revealing sensitive information like passwords or credit card details.
- User manipulation: Tricking users into divulging sensitive information or performing actions that compromise their security.
- Third-Party Integration Risks:
- Insecure APIs: Vulnerabilities or weaknesses in the APIs used for integrating with third-party services, allowing unauthorized access or data leaks.
- Untrusted libraries and SDKs: Using third-party libraries or software development kits with known vulnerabilities or malicious code.
- Lack of Compliance and Privacy Violations:
- Non-compliance with data protection regulations: Failure to adhere to legal requirements, such as GDPR, CCPA, or industry-specific regulations.
- Privacy policy violations: Collecting or using user data in ways that contradict stated privacy policies or user consent.
Best Practices To Ensure Mobile App Security
Ensuring mobile app security is of utmost importance in today’s interconnected world. By incorporating these s, you can significantly enhance the security posture of your applications and protect user data from potential threats.

- Secure Coding Practices: Employing secure coding practices involves using a reliable development framework and adhering to industry-standard coding techniques. By implementing input validation and output encoding, you can prevent common vulnerabilities like SQL injection or Cross-Site Scripting (XSS) attacks. Avoid hardcoding sensitive information within the app’s code, as this reduces the risk of unauthorized access to credentials or keys. It’s important to regularly update third-party libraries to ensure that your app benefits from security patches and fixes for known vulnerabilities.
- User Authentication and Authorization: Robust user authentication and authorization mechanisms are crucial for app security. Implementing robust authentication methods like multi-factor authentication (MFA) or biometric authentication adds an extra layer of protection beyond passwords. Enforcing secure password policies, such as complexity requirements and password hashing algorithms, helps guard against brute-force attacks. Proper session management techniques, like generating unique session IDs and expiring sessions after a period of inactivity, mitigate the risk of session-based attacks. Robust authorization controls ensure that users can only access authorized features, functions, and data within the app.
- Secure Network Communications: Secure communication protocols, such as HTTPS/TLS, encrypt the data transmitted between the app and servers, preventing eavesdropping or tampering. Verifying server certificates ensures that the app only communicates with trusted servers, reducing the risk of man-in-the-middle attacks. Implementing certificate pinning further enhances security by associating specific server certificates with the app, preventing fraudulent or malicious server impersonation. It’s important to avoid using insecure communication channels like HTTP and transmitting sensitive data in clear text, as this helps prevent unauthorized interception or data leakage.
- Data Storage and Encryption: Protecting sensitive data at rest is essential. Encrypting sensitive data stored on the device or in databases ensures its confidentiality, even if the device or storage medium is compromised. Employing access controls limits data access to authorized individuals or roles. Minimizing local storage of sensitive data on the device reduces the potential exposure if the device is lost or stolen. Implementing secure data deletion methods ensures that data is permanently removed from the device when it is no longer needed, mitigating the risk of unauthorized recovery.
- Regular Security Testing: Conducting thorough security testing, such as vulnerability assessments and penetration testing, helps identify vulnerabilities and weaknesses in the app’s security. Code reviews by experienced developers or security professionals assist in identifying security flaws and ensuring adherence to secure coding practices. Automated security testing tools can also assist in identifying common security weaknesses and vulnerabilities, providing an additional layer of testing and analysis.
- Privacy and Data Protection: Minimizing data collection to only what is necessary reduces the potential impact in case of a data breach or unauthorized access. Obtaining user consent for data collection and communicating the app’s privacy practices builds trust and ensures compliance with privacy regulations. Adhering to data protection regulations, such as GDPR or CCPA, ensures that user data is handled per legal requirements. Regularly reviewing and updating privacy policies helps maintain transparency and adapt to evolving privacy requirements and user expectations.
- Regular Updates and Patch Management: Keeping the app’s underlying operating system and frameworks up to date with the latest security patches and updates is crucial to address known vulnerabilities. Promptly addressing reported security vulnerabilities and releasing patches or updates to users helps protect against potential exploitation. Encouraging users to keep their devices and apps up to date through reminders or automatic update mechanisms ensures they benefit from the latest security fixes and enhancements.
To secure user data and uphold user trust, security, and privacy must be given top priority while developing apps. Developers can improve the security posture of their mobile applications by putting best practices into practice, such as secure coding, strong authentication, secure network communications, data encryption, routine security testing, and adherence to privacy legislation.
We at Black Widow Tech are aware of the importance of creating safe and secure mobile applications. The most recent industry standards and recommended procedures for app security are well-known to our team of skilled developers and security specialists. To make sure that our apps are built on a solid security basis, we adhere to careful procedures and use secure coding practices.
We place a high priority on user authentication and authorization, enhancing app security by utilizing sophisticated authentication techniques like multi-factor authentication and biometric authentication. Secure network communication methods like HTTPS/TLS are incorporated into our development process to encrypt data transmission and guard against hacking or manipulation.
We place a high priority on data security, and to protect sensitive information, we use strong data storage and encryption procedures. Regular security testing, such as penetration testing and vulnerability assessments, enables us to spot potential vulnerabilities early on and take proactive measures to fix them.
In addition, Black Widow Tech is dedicated to maintaining customer privacy and adhering to data protection laws. We make sure that only the essential user data is collected and stored, that user consent is properly obtained, and that privacy regulations are followed. To safeguard the privacy and security of our customers, we keep up with changing privacy standards.
By choosing Black Widow Tech as your mobile app development service provider, you can trust that your app will be developed with a strong emphasis on security and privacy. We strive to deliver safe, secure, and reliable mobile applications that protect user data and provide a trustworthy user experience.
Investing in robust security measures during the app development process not only safeguards sensitive information but also helps build user confidence and loyalty. Choose Black Widow Tech for your app development needs and embark on a journey toward creating a safe and secure mobile app that users can trust.
